Delete a Secret Key
Remove unused or compromised API keys to maintain security and manage access to your organization.
Delete secret keys that are no longer needed or have been compromised to maintain security and prevent unauthorized access to your organization's resources.
Before you delete
- Deletion is immediate and permanent — Applications using the key will lose access instantly
- Cannot be undone — You must create a new key if you delete one by mistake
- Update your applications — Ensure all applications have switched to a new key before deleting the old one
- Consider rotation schedule — Regularly rotate keys as a security best practice
When to delete a secret key
Delete keys in these situations:
- Compromised security — The key was accidentally exposed or shared
- No longer needed — The application or integration is decommissioned
- Regular rotation — Part of scheduled security maintenance
- User departure — Keys created by users who have left the organization
- Testing completed — Development or testing keys no longer required
Navigate to secret keys
-
Click on your organization name in the top navigation bar
-
Select Secret Keys from the sidebar menu
-
Locate the key you want to delete in the keys table
Delete a secret key
-
Find the key you want to remove in the Secret Keys table
-
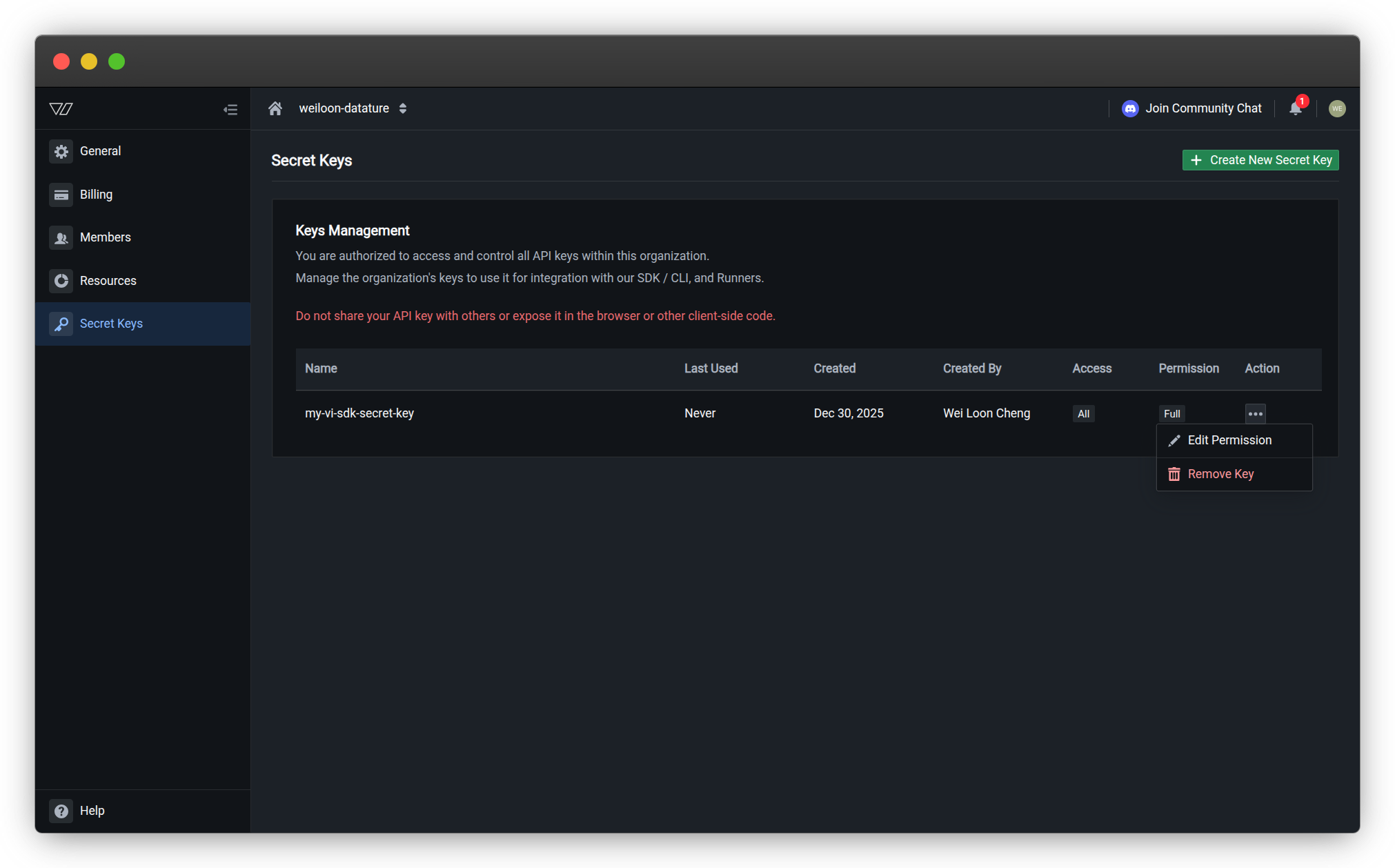
Click the action menu (⋯) in the Action column for that key
-
Select Remove Key from the dropdown menu
Delete action menuThe action menu provides two options:
- Edit Permission — Modify the key's access and permissions
- Remove Key — Delete the key permanently
-
A confirmation dialog appears asking you to confirm the deletion
-
Click Confirm or Remove to permanently delete the key
Immediate effectOnce deleted, the key is immediately revoked. Any application or service using this key will receive authentication errors on the next API request.
Verify deletion
After deletion, the key is removed from the Secret Keys table and can no longer be used to authenticate with Datature Vi services. Applications using the deleted key will encounter authentication errors.
Update applications after deletion
If you deleted a key that was actively in use, update your applications with a new key:
-
Create a new secret key with the appropriate permissions
-
Update your application configuration with the new key
Update Vi SDK with new secret key
Direct initialization:
import vi
# Update with new key
client = vi.Client(
secret_key="your-new-secret-key-here",
organization_id="your-organization-id-here"
)Using environment variables:
# Update environment variables
export DATATURE_VI_SECRET_KEY="your-new-secret-key"
export DATATURE_VI_ORGANIZATION_ID="your-organization-id"Then initialize the client:
import os
import vi
client = vi.Client(
secret_key=os.getenv("DATATURE_VI_SECRET_KEY"),
organization_id=os.getenv("DATATURE_VI_ORGANIZATION_ID")
)Configuration files:
Update any configuration files, deployment settings, or CI/CD pipelines that reference the old key.
Security best practices
Schedule periodic key rotation (e.g., every 90 days) to minimize risk from undetected compromises
Check the "Last Used" column to identify inactive keys that can be safely deleted
Create different keys for production, staging, and development environments
Use descriptive names to track which application or service uses each key
Next steps
Generate a new API key to replace the deleted one
Learn how to use secret keys with the Vi SDK
Need help?
We're here to support your VLMOps journey. Reach out through any of these channels:
Updated about 1 month ago